- This is the default BGP behavior. Just turn on BGP, configure it correctly and everything is ok. No really worries about this.
- Same for this point, this is the default BGP behavior.
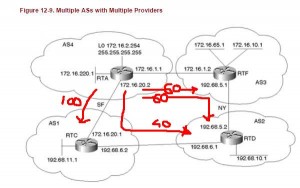
- For the first part: this is the default BGP behavior. (hey this lab seems too easy!). For the second part: we don’t want AS4 to go to AS2 via AS1 unless link between AS4 and AS3 is down. We can reach this target using local preference. But anyway we also want to use the community attribute for simplify the policy for adding new customers. So let’s do this conf in RTC:
router bgp 1 network 192.68.11.0 neighbor 172.16.20.2 remote-as 4 neighbor 172.16.20.2 send-community neighbor 172.16.20.2 route-map setcommunity out neighbor 192.68.6.1 remote-as 2 no auto-summary
route-map setcommunity permit 10 set community 4:40
Let’s start with the route map setcommunity: we are just going to set a community, nothing more.
The same mirrored configuration should be applied to RTD.
Now let’s go to configure some actions if we are going to see this community coming to our AS4.
This is what we should do to into RTA:
router bgp 4 network 172.16.220.0 mask 255.255.255.0 neighbor 172.16.1.2 remote-as 3 neighbor 172.16.1.2 route-map CHECK_COMMUNITY in neighbor 172.16.20.1 remote-as 1 neighbor 172.16.20.1 route-map CHECK_COMMUNITY in no auto-summary ip community-list 2 permit 4:40 ip community-list 3 permit 4:60 route-map CHECK_COMMUNITY permit 10 match community 2 set local-preference 40 route-map CHECK_COMMUNITY permit 20 match community 3 set local-preference 60 route-map CHECK_COMMUNITY permit 30 set local-preference 100
With the commands above we are just checking if from our neighbors in RTA we are receiving some routes with the community attributes. If so we do set:
- a local preference of 40 if community is 4:40
- a local preference of 60 if community is 4:60
- a local preference of 100 by default
Then we will proceed setting up the RTF router:
router bgp 3 network 172.16.10.0 mask 255.255.255.0 network 172.16.65.0 mask 255.255.255.192 neighbor 172.16.1.1 remote-as 4 neighbor 172.16.1.1 send-community neighbor 172.16.1.1 route-map setcommunity out neighbor 192.68.5.2 remote-as 2 no auto-summary route-map setcommunity permit 10 set community 4:60
In a nutshell all the routes from RTF are tagged with community 4:60 and they are going to have a preference of 60 in RTA.
Let’s check what is the result of this configuration:
RTA#sh ip bgp BGP table version is 11, local router ID is 172.16.2.254 Status codes: s suppressed, d damped, h history, * valid, > best, i - internal, r RIB-failure, S Stale Origin codes: i - IGP, e - EGP, ? - incomplete
Network Next Hop Metric LocPrf Weight Path * 172.16.1.0/24 172.16.1.2 0 60 0 3 i *> 0.0.0.0 0 32768 i *> 172.16.2.0/24 0.0.0.0 0 32768 i * 172.16.10.0/24 172.16.20.1 40 0 1 2 3 i *> 172.16.1.2 0 60 0 3 i * 172.16.20.0/24 172.16.20.1 0 40 0 1 i *> 0.0.0.0 0 32768 i * 172.16.65.0/24 172.16.20.1 40 0 1 2 3 i *> 172.16.1.2 0 60 0 3 i *> 172.16.220.0/24 0.0.0.0 0 32768 i * 192.68.5.0 172.16.20.1 40 0 1 2 i *> 172.16.1.2 0 60 0 3 i * 192.68.6.0 172.16.20.1 40 0 1 2 i *> 172.16.1.2 60 0 3 2 i * 192.68.10.0 172.16.20.1 40 0 1 2 i *> 172.16.1.2 60 0 3 2 i *> 192.68.11.0 172.16.1.2 60 0 3 2 1 i Network Next Hop Metric LocPrf Weight Path * 172.16.20.1 0 40 0 1 i
From this show ip bgp I can see:
172.16.10.0 and 172.16.10.65 with two paths and we don’t want this. We don’t want AS4 able to reach AS3 via AS1 and AS2. Anyway we can observe that one route has a preference of 40 and the other of 60.
Same for 192.68.10.0: one route has 60 and the other 40. The best path is through AS3 and we want this.
Next step is going to be work with path filtering.
4) AS AS4 should not be able to reach AS3 via AS1 and AS2.
For reaching this target we are going to use the ip as-path access lists:
ip as-path access-list 2 permit _2_ ip as-path access-list 10 permit ^$ ip as-path access-list 10 permit ^2$
Ther first one, the number 2, is going to match all the routes with 2 in the AS path.
The as-path access list 10 is going to match local routes and routes with 2 as per last AS in the path.
Then we have to apply a filter list that matches this conditions:
Router bgp 1 neighbor 172.16.20.2 filter-list 10 out
and then let’s go to apply the community 4:40 only for the matches in ip as-path access-list 2:
route-map setcommunity permit 10 match as-path 2 set community 4:40 route-map setcommunity permit 20
The same configuration, but mirrored, has to be applied on RTD.
After a clear ip bgp * we can see the final result:
RTA#sh ip bgp BGP table version is 13, local router ID is 172.16.2.254 Status codes: s suppressed, d damped, h history, * valid, > best, i - internal, r RIB-failure, S Stale Origin codes: i - IGP, e - EGP, ? - incomplete Network Next Hop Metric LocPrf Weight Path *> 172.16.1.0/24 0.0.0.0 0 32768 i * 172.16.1.2 0 60 0 3 i *> 172.16.2.0/24 0.0.0.0 0 32768 i *> 172.16.10.0/24 172.16.1.2 0 60 0 3 i * 172.16.20.0/24 172.16.20.1 0 100 0 1 i *> 0.0.0.0 0 32768 i *> 172.16.65.0/24 172.16.1.2 0 60 0 3 i *> 172.16.220.0/24 0.0.0.0 0 32768 i * 192.68.5.0 172.16.20.1 40 0 1 2 i *> 172.16.1.2 0 60 0 3 i * 192.68.6.0 172.16.20.1 40 0 1 2 i *> 172.16.1.2 60 0 3 2 i * 192.68.10.0 172.16.20.1 40 0 1 2 i *> 172.16.1.2 60 0 3 2 i *> 192.68.11.0 172.16.20.1 0 100 0 1 i
So:
172.16.10.0 and 172.16.65.0 are reachable only via RTF with a preference of 60
192.68.10.0 is reachable via two ways but with highest preference via AS3
AS4 cannot reach AS3 via customer’s ASs.
If you are doing this lab and you need some info don’t hesitate to leave a comment.
Net file for GNS3:
lab003 – BGP – Multiple ASs with Multiple Providers
Config files:
RTF RTA RTC RTD